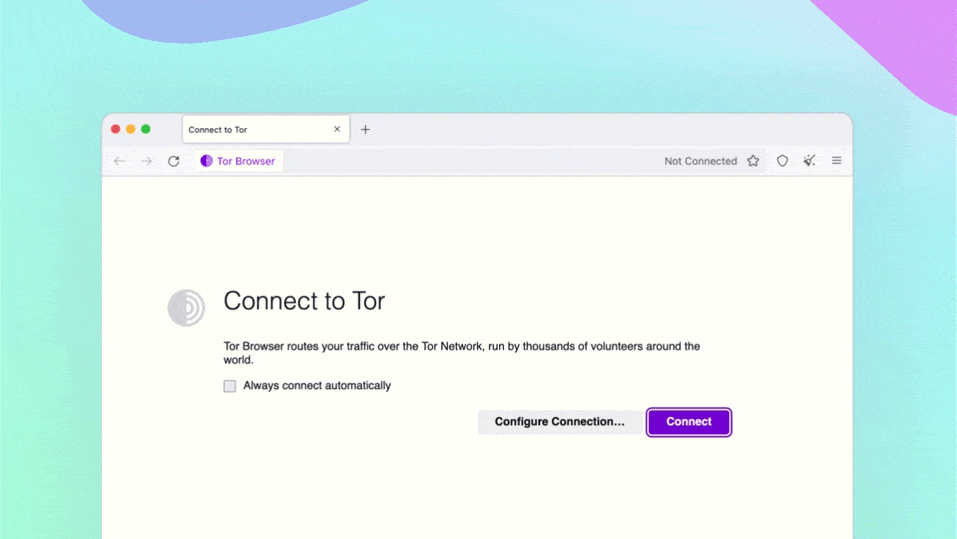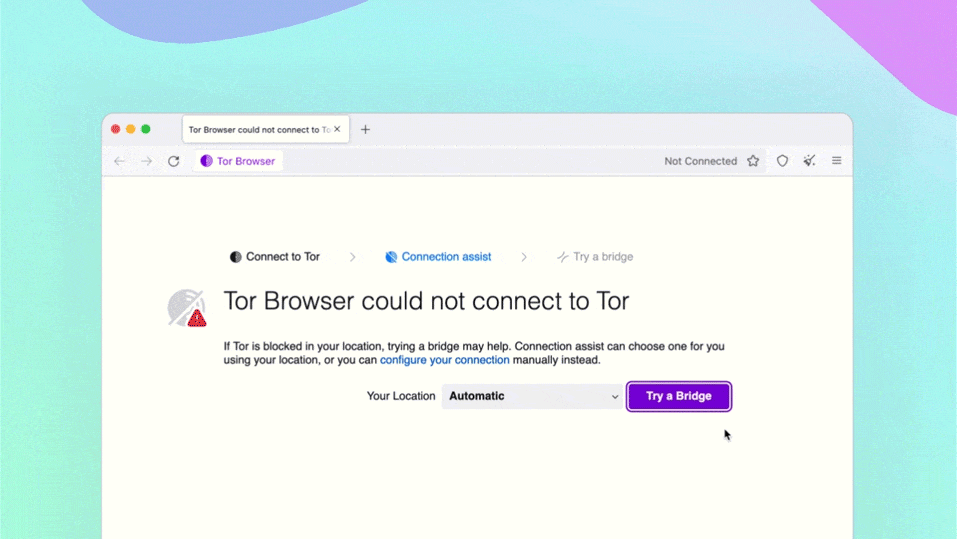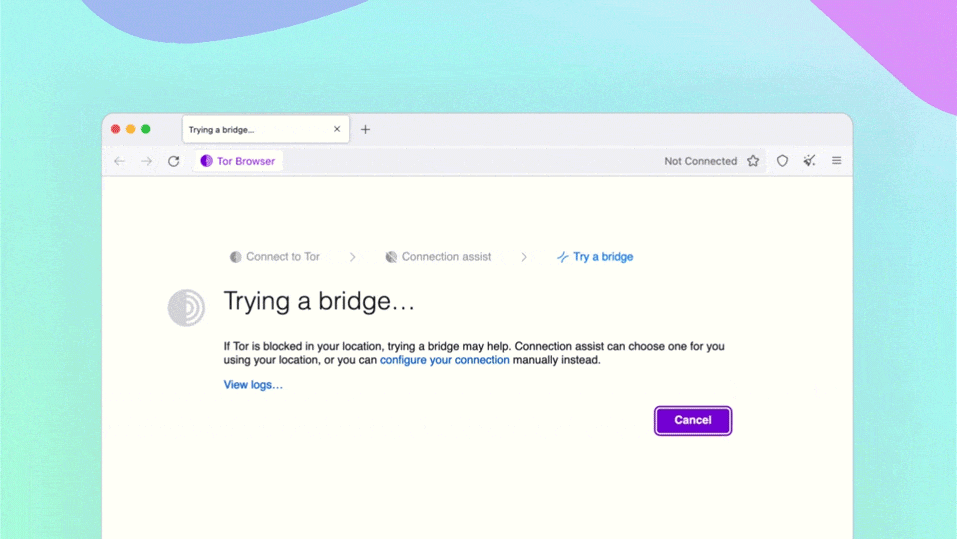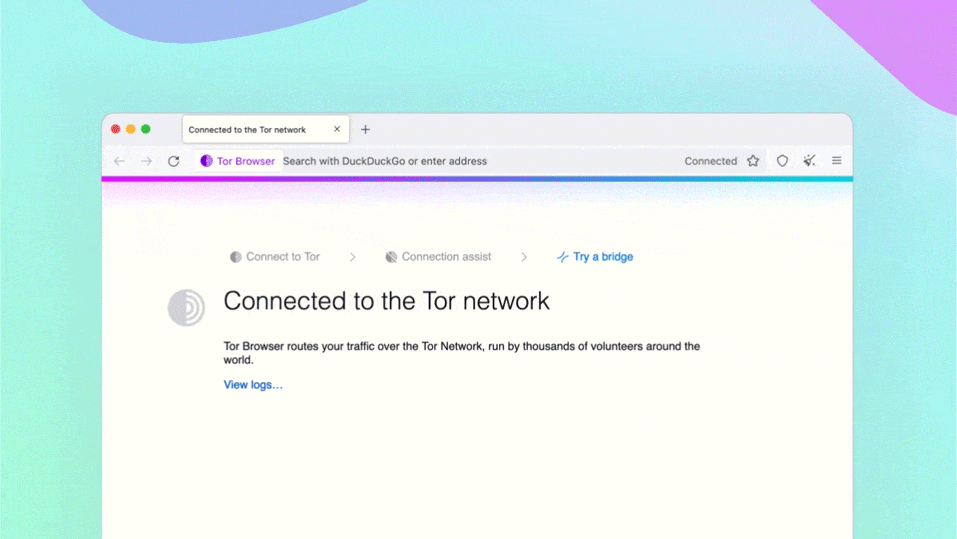
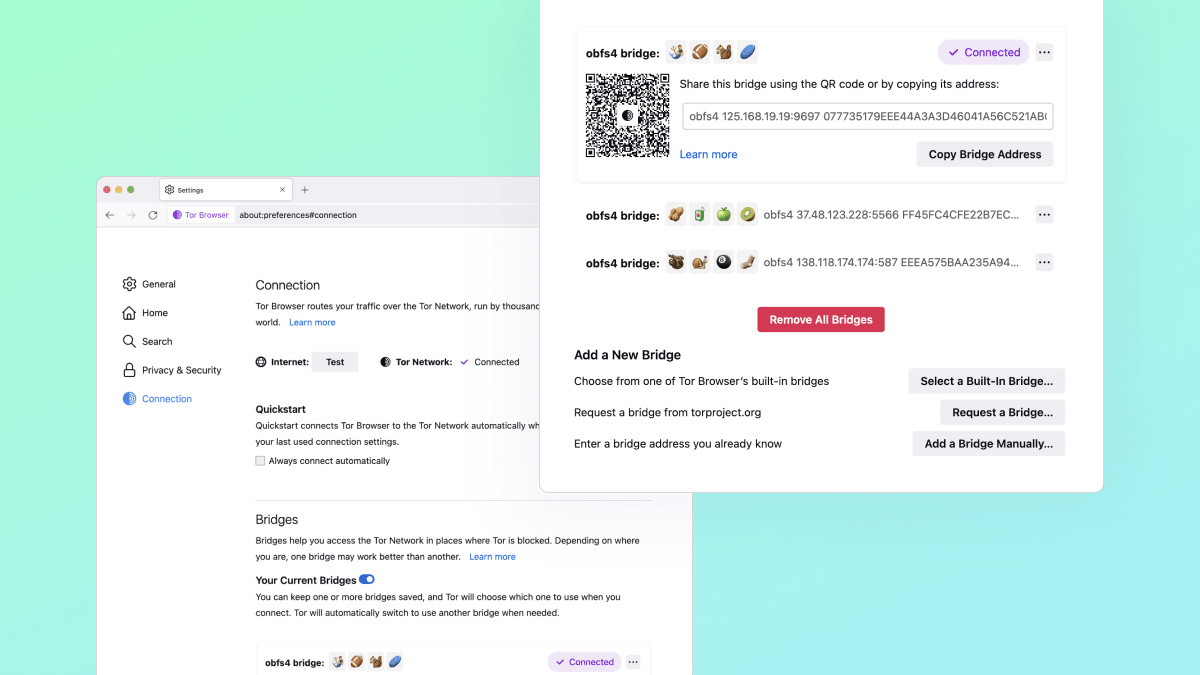
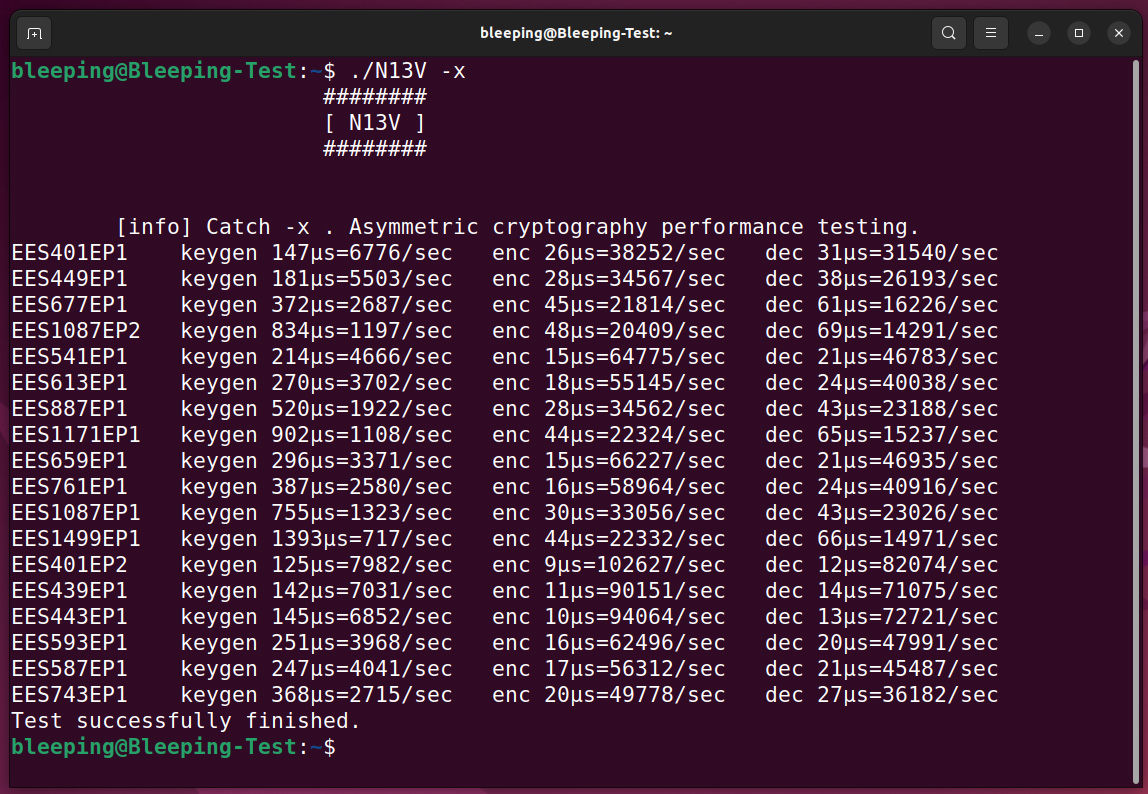
On July 7th, 2011, eleven years ago, JDK 7 was released. In some ways, it was one of the more significant releases of Java. Indeed, there were some excellent technical features: Project Coin gave us things like try-with-resources, strings in switch and multi-catch.
However, it was two non-technical aspects of JDK 7 that made it important.
The first was that it was the first release since Oracle acquired Sun Microsystems. The Java community had been unsure how Java would fare under Oracle, so this release showed a solid commitment to the platform (which has been maintained since then).
The second was even more important: the fact that a Java SE specification was published through the Java Community Process. Due to issues around the availability of the TCK and the Apache Harmony project, new versions of OpenJDK had been stalled since December 2006. To put this into context, the time between JDK 6 and JDK 7 (one release) was one month longer at four years and seven months than between JDK 9 and JDK 18 (nine releases). Getting things moving again was vital to keeping Java relevant to developers as applications and architectures evolved.
Another significant date for JDK 7 is July 19th this year. That is when the last update will be made available from Oracle, even for commercially supported users. It is the end of what Oracle terms Extended Support.
However, it turns out that there are still a significant number of people who are using JDK 7. In almost all cases, this is not because users don’t want to move to a newer version; they’re just not in a position to be able to do so. In many ways, this is one of Java’s strengths: you can just keep using an older version because your application doesn’t need features from newer releases. If you can keep your implementation of JDK 7 updated with relevant security patches and bug fixes, why change?
Extending Support of JDK 7
Fortunately, if you are one of those users who are not in a position to migrate from JDK 7 to a newer release, Azul has a solution for you. We will continue to provide updates (scheduled quarterly ones and any out-of-bounds) to our Zulu builds of OpenJDK 7 until at least December 2027 (see our Support Roadmap for more information). Our highly skilled team of Java and JVM engineers will backport all applicable changes from the current release of Java to JDK 7.
That’s another five and a half years without figuring out how to migrate those trusty applications and with peace of mind that your Java runtime is as secure as possible.






.png)